Technology is an invention designed to facilitate and simplify the way of life of the human race. Today is the age of information technology. Security Risk Management in organizations involves the use of various tools to mitigate potential security threats.
Hand-held metal detectors, voice loggers, and rapid communication systems are just a few examples of the tools used in security risk management. These tools help organizations detect, respond to, and mitigate security incidents. By implementing these tools and practices, organizations can effectively manage security risks and protect their assets, reputation, and customers trust.
Security management principles and applications with examples
The situation of the use of technology seems to be very different between developed countries and developing nations the use of information and technology is essential to improve the management system, produce capable and efficient manpower, bridge the gap between access to information and communication technology, and promote continuous and lifelong learning.
Walk Through Gate:
The walkthrough gate is a security management tool. A walk-through gate is a type of electronic door security management tool built with a definite foundation and structure in mind from the point of view of security. It can be found in various models and textures.
It is actually called Walkthrough Metal Detector. But it can be found in any texture like this.
It consists of various Electronic Devices. This generates EMF (Electro Magnetic Field) and the Walkthrough Gate is based on the same Electro Magnetic Field Detecting Principal. Therefore, Walkthrough Gate plays an important role in finding out how much metal is in the person or belongings that have passed through Walkthrough Gate.
Operating System:
The walkthrough gate has two legs on the right and left and the mainboard is at the top. Metal Sensor and Countable Counter are placed on both the legs and the sensor on the legs sensor the metal as it passes through the Walkthrough Gate.
In this way, the signal of the metal sensor goes to the mainboard. The mainboard gives information according to the type of signal in which the metal is detected. So that any person who goes through that door can know whether he has metal or not. A Walkthrough Gate can be found today and tomorrow to find out where metal is kept for security risk management.
Hand-Held Metal Detector
A handheld metal detector is a handheld device that detects metal. A handheld metal detector is a type of electronic device that is designed with a certain size and shape in mind from a security point of view.
It provides information through any signal or sound when any metal enters its fixed area. It has a voice and indicator as well as vibrations that can be found in the market. And used for security risk management.
Voice Logger
A voice logger is a type of electronic device that records the sound of any radio, telephone, or other medium transmitted 24 hours a day. With the help of this, the recorded data can be reused in the required time. All the data recorded in the system can be found by looking at its display.
Voice Logger is usually used for security purposes. It is also widely used in security organizations and private organizations. Voice logger is used to recording voices of Telephone systems and Communication Equipment Radio Set in security organizations
Voice Logger has also been used by Police. Police have recorded Voice Logger Equipment on the hotline Telephone Number 100 connected to the operating room under the Metropolitan Police Office in the Valley. With the help of Voice Logger, you can record audio and play it back and get the necessary information.
Front View of Voice Logger:
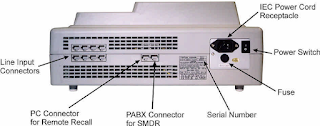
Rear (Back) View of Voice Logger:
Frequency Jammer:
Frequency Jammer is a security management tool and technique to reduce risk. A frequency Jammer is a device that blocks the radio signal. A device with a more powerful signal is used to block a running radio signal.
For example,
To block the signal of a running mobile phone, the device with more power of the same frequency is turned on due to which the signal of the mobile phone is lost. the movement of special and very special people.
Rapid Communication System
There are 12 antennas connected to the roof of the vehicle. These antennas have Frequency Range HF, VHF, UHF, CDMA, GPS, WiMAX, etc. whose equipment is connected inside the vehicle. The battery is connected to Power Supply to operate these devices. Also, UPS and generators are connected.
The sound comes from the generator we have but Noise Free Generators are suitable for running such equipment. Jammers are often used in VVIPs such as foreign presidents, prime minister visits, medical council exams, etc. because after using this device, no terrorist can detonate explosives remotely through any frequency.
Frequency jammers jam such frequencies. The jammer we have has an estimated capacity radius of 150 meters. It is used for limited coverage areas and where there is no public telecommunication network or weak signal. It is also called Rapid Communication System as it can be used for emergency communication and can be set up in 15 minutes.
The sound comes from the generator we have but Noise Free Generators are suitable for running such equipment. Jammers are often used in VVIPs such as foreign presidents, prime minister visits, medical council exams, etc. because after using this device, no terrorist can detonate explosives remotely through any frequency.
Frequency jammers jam such frequencies. The jammer we have has an estimated capacity radius of 150 meters. It is used for limited coverage areas and where there is no public telecommunication network or weak signal. It is also called Rapid Communication System as it can be used for emergency communication and can be set up in 15 minutes.
Application of Rapid Communication System
To monitor the security of the main programs. To protect the city dynamically. In disaster management. VIP protection. To broadcast live video from remote areas. Police raids, sieges, etc.
Baggage Scanner
A portable Baggage Scanner is used to check small luggage - Hand Bags and Heavy Duty Scanner to check large luggage - Cargo or Large Bags.
It has parts including Monitor, Scanner, Belt, and Bag Stand. To check the items prohibited by law including explosives/hand weapons kept inside the bag. If there is any suspicion while scanning the contents of the bag or if any suspicious item is seen on the monitor, the operator can open the bag and check.
It is usually placed at the entrance of the airport and the venue with very special/exclusive people. It requires skilled people to operate. Generally, the luggage and technical / store communication with the Police is done by the communicators, and the airport staff is done by the operators. Putting human organs in machine mode instead of baggage scanning is not suitable for health reasons.
Vehicle Bottom Scanner
This is to check the items prohibited by law, including explosives/handguns hidden under the vehicle. Portable Type Small Vehicles - Heavy Duty Type Larger Vehicles are used to check hidden goods. It contains Scanner, Camera, Connectors with Cable Set, Monitor, and other parts.
It is often used to check illegal items hidden under the car at the entrance of the venue/building where very special people are present. Skilled people are needed to operate it. Generally, the security agency has been working from technical / store side communication and operator side from vehicle side staff.
Conclusion
In conclusion, effective Security Risk Management is important for organizations to protect their assets, reputation, and customers' trust. This involves identifying potential security threats, assessing their impact, and implementing measures to mitigate them. By adopting best practices and utilizing these tools, organizations can effectively manage security risks and ensure their ongoing safety and success.
Read More...
- 13 Practice To Protect Yourself In Cyber World. (Click here...)
- 15 Best Vehicle Detection Sensors in 2023. (Click here...)



%20view%20of%20voice%20logger.jpg)




